|
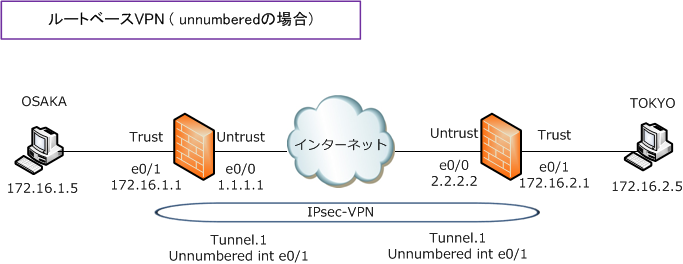
◆ ルートベースVPN 設定例
set hostname SSG5-1
set int ethernet0/0 zone Untrust
set int ethernet0/0 ip 1.1.1.1/24
set int ethernet0/0 route
set int ethernet0/1 zone Trust
set int ethernet0/1 ip 172.16.1.1/24
set int ethernet0/1 route
set interface tunnel.1 zone Trust
set interface tunnel.1 ip unnumbered interface ethernet0/1
set ike gateway P1TOKYO address 2.2.2.2 outgoing-int e0/0 preshare juni1234
sec-level standard
set vpn P2TOKYO gateway P1TOKYO sec-level standard
set vpn P2TOKYO bind interface tunnel.1
set route 172.16.2.0/24 interface tunnel.1
set route 0.0.0.0/0 interface ethernet0/0 gateway 1.1.1.254
|
set hostname SSG5-2
set int ethernet0/0 zone Untrust
set int ethernet0/0 ip 2.2.2.2/24
set int ethernet0/0 route
set int ethernet0/1 zone Trust
set int ethernet0/1 ip 172.16.2.1/24
set int ethernet0/1 route
set interface tunnel.1 zone Trust
set interface tunnel.1 ip unnumbered interface ethernet0/1
set ike gateway P1OSAKA address 1.1.1.1 outgoing-int e0/0 preshare juni1234
sec-level standard
set vpn P2OSAKA gateway P1OSAKA sec-level standard
set vpn P2OSAKA bind interface tunnel.1
set route 172.16.1.0/24 interface tunnel.1
set route 0.0.0.0/0 interface ethernet0/0 gateway 2.2.2.254
|
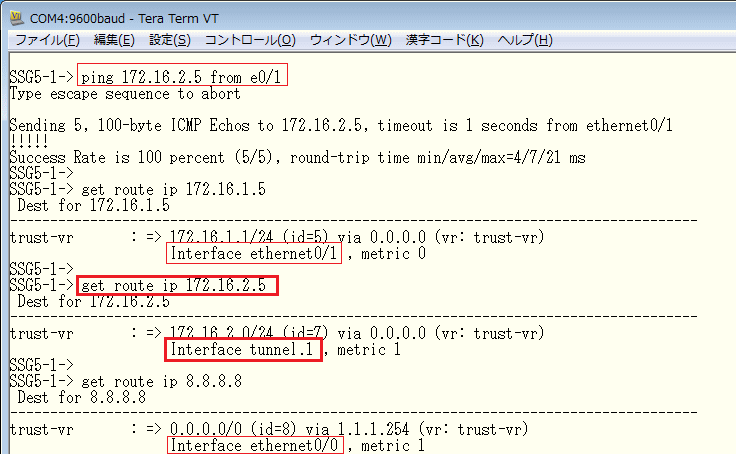
pingでエンドツーエンドで疎通をさせてトンネルを確立。 get route ipで宛先ネットワークに対しどのI/Fを使用しているかを確認。
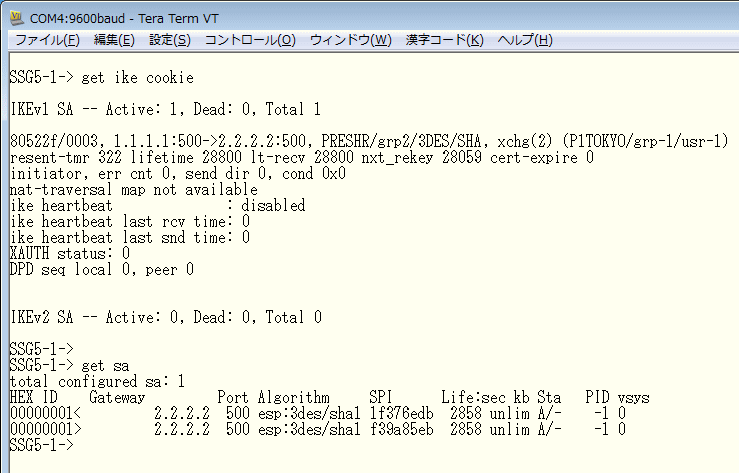
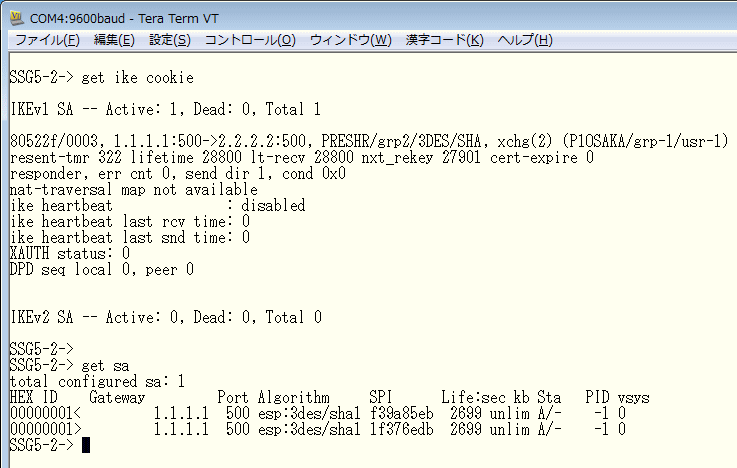
以下は、ルートベースVPNのIPsec-VPNが成功している際のステータスです。見方は、ポリシーベースVPNの時と同じ方法です。
◆ ポリシーベースVPN 設定例 ( CiscoルータとJuniper SSGとの接続 )
SSGとCiscoルータとでIPsec-VPN接続を行う場合のポリシーベースVPNの設定例は以下のとおりです。
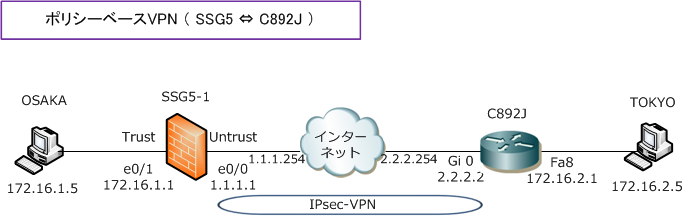
set hostname SSG5-1
set int ethernet0/0 zone Untrust
set int ethernet0/0 ip 1.1.1.1/24
set int ethernet0/0 route
set int ethernet0/1 zone Trust
set int ethernet0/1 ip 172.16.1.1/24
set int ethernet0/1 route
set route 0.0.0.0/0 int e0/0 gateway 1.1.1.254
set ike gateway P1TOKYO address 2.2.2.2 outgoing-int e0/0 preshare JUNI
sec-level standard
set vpn P2TOKYO gateway P1TOKYO sec-level standard
set address Trust OSAKANW 172.16.1.0/24
set address Untrust TOKYONW 172.16.2.0/24
set policy id 1 from Trust to Untrust OSAKANW TOKYONW ANY tunnel vpn P2TOKYO
set policy id 2 from Untrust to Trust TOKYONW OSAKANW ANY tunnel vpn P2TOKYO
|
crypto isakmp policy 1
encr 3des
hash sha
authentication pre-share
group 2
crypto isakmp key JUNI address 1.1.1.1
crypto ipsec transform-set IPSEC esp-3des esp-sha-hmac
crypto map M-ipsec 1 ipsec-isakmp
set peer 1.1.1.1
set transform-set IPSEC
match address A-ipsec
interface GigabitEthernet0
ip address 2.2.2.2 255.255.255.0
duplex auto
speed auto
crypto map M-ipsec
interface FastEthernet8
ip address 172.16.2.5 255.255.255.0
duplex auto
speed auto
ip route 0.0.0.0 0.0.0.0 2.2.2.254
ip access-list extended A-ipsec
permit ip 172.16.2.0 0.0.0.255 172.16.1.0 0.0.0.255
|
※ Cisco側は show crypto isakmp sa と show crypto ipsec sa コマンドによりステータスを確認しましょう。
※ Ciscoルータで以下のようなメッセージが出力される場合はSSG、Cisco両方を再起動すれば解決する場合があります。
%CRYPTO-4-IKMP_NO_SA: IKE message from 1.1.1.1 has no SA and is not an
initialization offer
%CRYPTO-4-RECVD_PKT_INV_SPI: decaps: rec'd IPSEC packet has invalid spi
for destaddr=2.2.2.2,
prot=50, spi=0xF39A85EC(4086990316), srcaddr=1.1.1.1
|





